Improving web performance & security with TLS 1.3

HTTPS is a must these days. And there’s a way to make it even faster and more secure. CDN77 now supports the latest TLS 1.3 with 0-RTT to boost HTTPS performance and security all over the world.
About TLS and SSL protocols
TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are cryptographic protocols that secure communications over the computer network.
While the term “SSL” is commonly associated with security certificates that enable HTTPS connections, its name is rather misleading. The thing is that SSL protocols aren’t considered secure since 2015 but certificates aren’t dependent on protocols. We, therefore, hope that your “SSL cert” is actually running on newer, faster and more secure TLS protocols. You can easily check your SSL/TLS setup here.
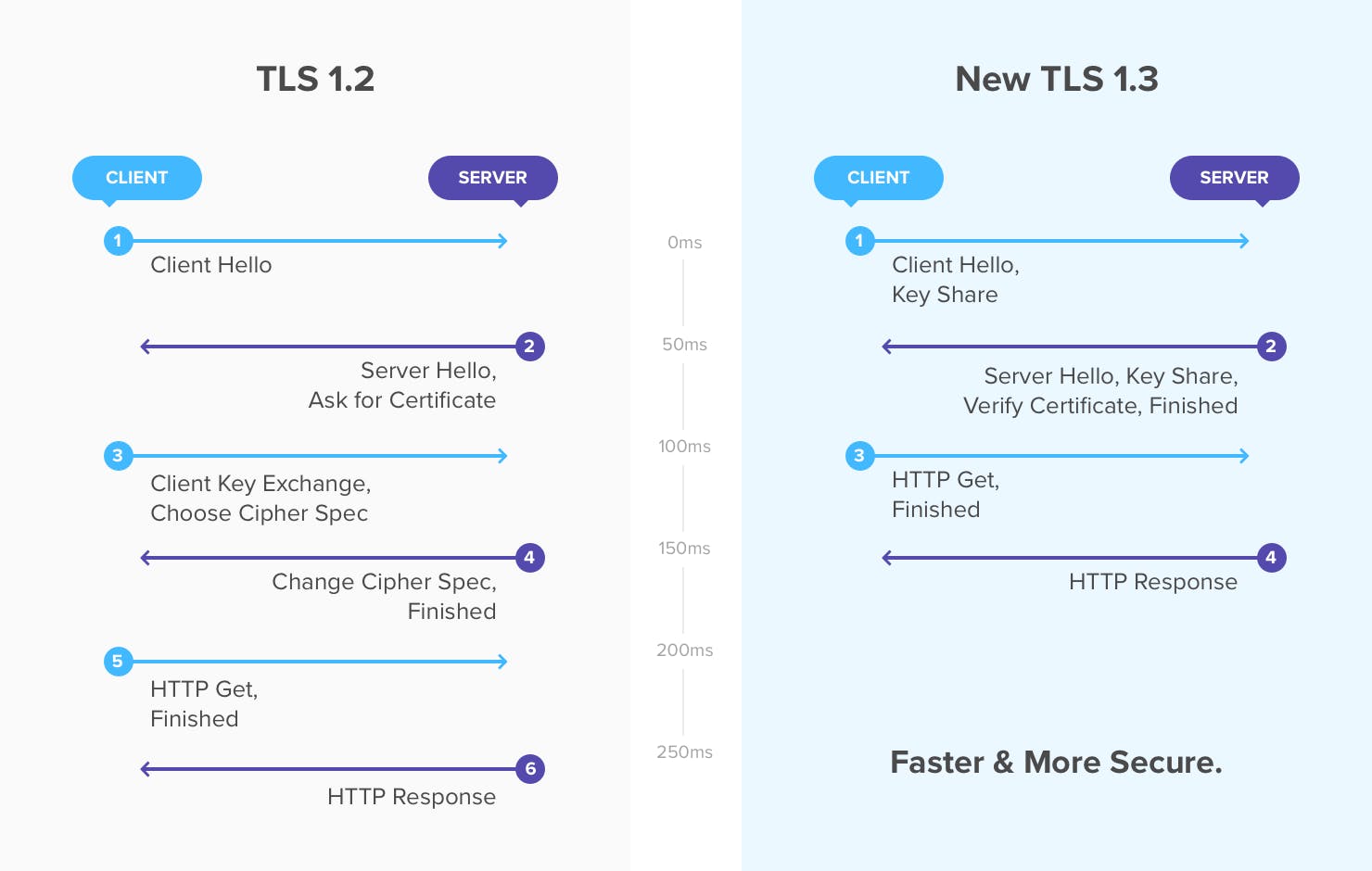
The best of TLS 1.3 – Abbreviated TLS Handshake
Prior to any data transfer, a proper handshake needs to be completed between the client and the server to establish an HTTPS connection. They agree on cypher suites, secret keys, and other important parameters to make the connection safe.
TLS 1.3 handshake was reduced to one round trip time (1-RTT). In other words, a client doesn’t need to contact the server as many times as in previous versions (2-RTT in TLS 1.2) to establish or resume HTTPS connections.

Displayed values are used as an example.
Speed and security go hand in hand. The abbreviated TLS handshake is also more secure as it encrypts a larger part of previously unprotected communication and removes several old and unused mechanisms, such as secure hash algorithm 1 (SHA-1), Digital Signature Algorithm (DSA) certificates or static RSA key exchange.
Every millisecond of reduced latency for your visitors is important, especially on mobile devices. HTTPS connections powered by HTTP/2 and TLS 1.3 offer unparalleled performance. CDN77 also provides free TLS certificate options for your CDN URL or CNAME. It’s the perfect package to deliver your content in the safest and fastest way.
Availability
TLS 1.3 has been deployed on all of our global edge servers. It’s already activated, free of charge. Your HTTPS connections are therefore powered by TLS 1.3 if you’re a CDN77 customer.
Until now, we only talked about server-side support but we can’t forget about the client.
Chrome or Firefox already support TLS 1.3 by default. It’s a matter of time until Safari, Opera and other web browsers come along.
Update 2023: TLS 1.3 is supported by all major web browsers.
Does your server or CDN support TLS 1.3?
Paste your domain URL into our TLS Checker and reveal the enabled SSL/TLS configuration on your server or CDN within seconds.
TLS 1.3 key features & comparison with TLS 1.2
We’ve only scratched the surface so far. There’s so much to TLS 1.3. We selected just a few concepts to illustrate its benefits. Cryptography and network ninjas will appreciate the TLS 1.3 RFC specifications.
How does TLS handshake work?
TLS 1.2 initializes the connection with a dialogue to agree on a certain encryption type. Once the client and server agree, they begin sharing encryption keys. The full handshake is no shorter than 2-RTT.
The reason for TLS 1.3 being faster is because this communication never takes place. Instead, the initial connection is an information from the client saying what it plans to access along with supported cypher, key agreements and other information. The server responds with the chosen cypher suite and also a key share. Since the server provides the key right away, the client cannot demand the use of older forms of encryption, hence making the connection more secure.
Technically, the client sends all the necessary information to establish a secure connection in the initial ‘Hello message’. It even calculates multiple pre-shared keys based on offered cypher suites. Once the server receives the initial ‘Hello message’, it provides a key to the client based on the chosen cypher suite.
0-RTT
TLS handshake for session resumption could be shorter in comparison with a new connection establishment. TLS 1.3 allows a Zero Round Trip Time Resumption leading to a faster and smoother experience for users returning to your website.
0-RTT doesn’t come with TLS 1.3 by default and has to be deployed separately. CDN77 supports it on all servers.
PSK (pre-shared key) mechanism
TLS 1.2 uses session IDs and tickets to enable session resumption. A server could decide whether to accept the resumption or to initiate a full TLS handshake. The resumption is achieved with slightly changed parameters from the previous handshake and continues in the existing TLS session using the same TCP connection.
This is considered unsafe and TLS 1.3 introduces a more secure method which is made possible by the PSK mechanism. It restarts a previous TLS session in a new TCP connection, using the same TLS parameters. Pre-shared keys can be agreed upon during the initial handshake and then used in subsequent handshake communication in order to perform resumption.
0-RTT can instantly resume all recently closed connections thanks to the PSK mechanism.
Authenticated Encryption with Associated Data (AEAD) algorithms
TLS 1.3 comes with a new set of cypher suites utilizing modern AEAD algorithms, made exclusively for the protocol. This is a form of encryption that provides the following key features to improve TLS security and reliability.
- Confidentiality
undefined - Authentication
undefined - Integrity
undefined
What’s coming next?
What are other hot topics in web performance and security world right now? Head to the web performance roundup post to learn more about experts’ predictions and expectations for 2018. It’s interesting to check the industry progress with such hindsight.
With CDN77, you can already benefit from the ultimate web performance package consisting of HTTP/2, Brotli and TLS 1.3. However, creating a faster and more secure web is a never-ending challenge. Stay tuned for the upcoming features and improvements!
Want to test TLS 1.3 right away? Get a free 14-days trial to boost your HTTPS performance worldwide. No credit card needed, no commitments.

Marketing